Securing your Compiled Configuration
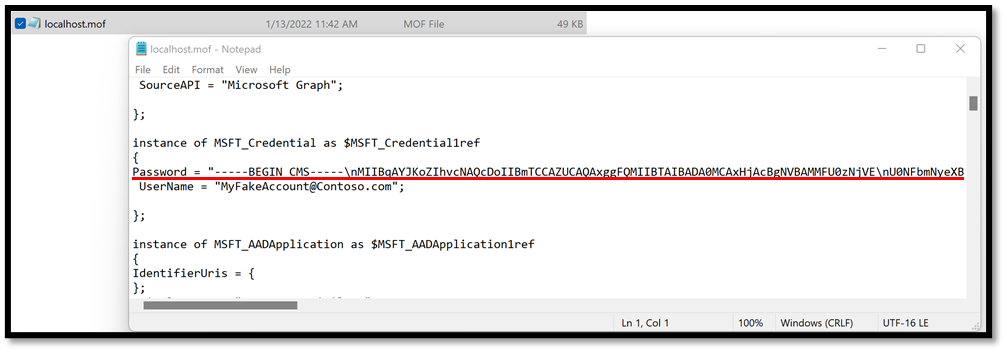
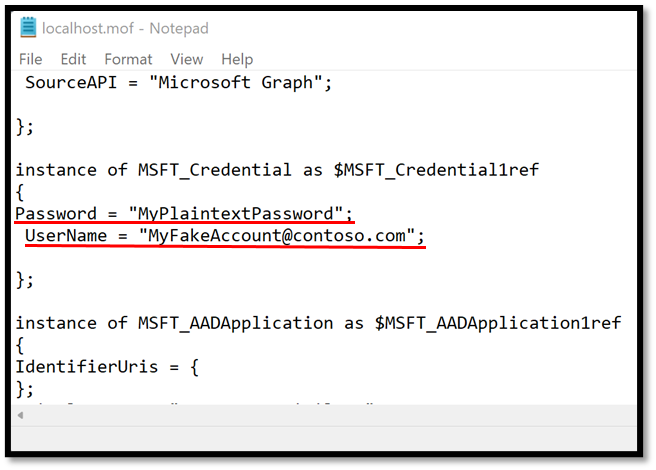
In the case where you are using credentials to authenticate to your tenant, you will be prompted to provide credentials at compilation time for your configuration. By default, these credentials will be stored as plain text in the resulting MOF file, which is a big security concern.
Creating an encryption certificate¶
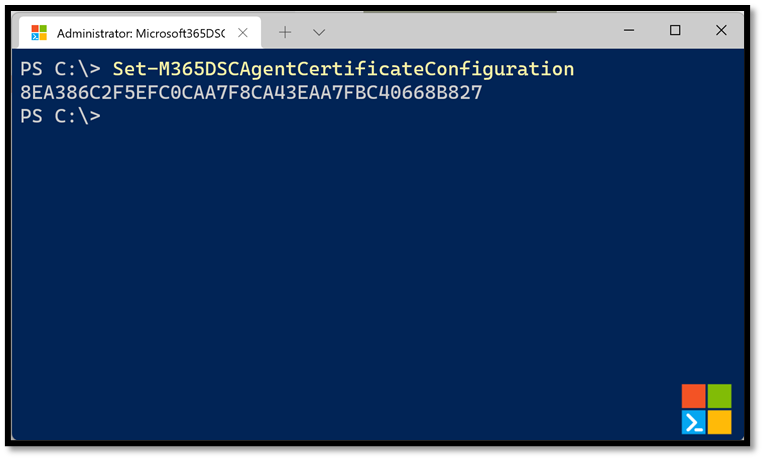
To remediate this, PowerShell DSC lets us use an encryption certificate to encrypt information about credentials in the MOF files. To make this process easier for users, Microsoft365DSC defines a function named Set-M365DSCAgentCertificateConfiguration which will automatically generate an encryption certificate and configure the PowerShell DSC engine on the system to use it for encrypting the MOF files. The cmdlet will return the Thumbprint for the newly generated certificate.
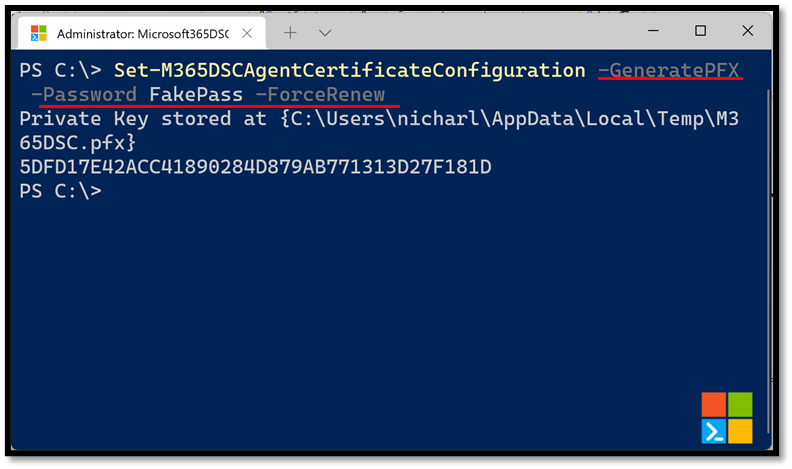
You can also have the cmdlet generate the private key for the certificate by using the -GeneratePFX switch and specifying a password with the -Password parameter. This will require you to also specify the -ForceRenew parameter so that a brand new certificate gets emitted.
Using certificates in the configuration¶
Once the certificate has been configured every time you do a snapshot of an existing tenant’s configuration, a new M365DSC.cer certificate file will be stored in the same directory as the configuration files. The ConfigurationData.psd1 will also contain a new entry under the localhost node that will point to this certificate, effectively telling DSC to use this file to encrypt credentials when compiling.
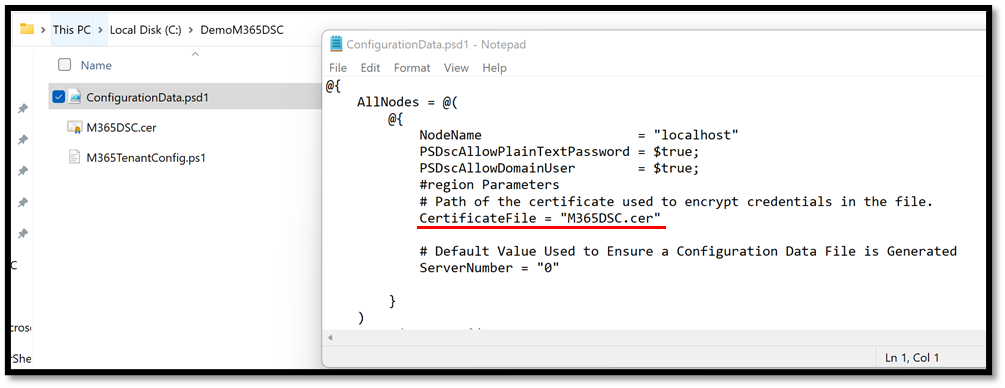
If you compile your configuration using the new certificate and take a look at your MOF file, you should see that the password for the credential object was successfully encrypted and is no longer stored in plaintext.